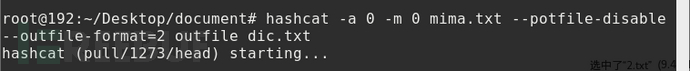
Hashcat claims to be the world's fastest password cracking tool.
2024-12-24 20:36:31
Hashcat claims to be the fastest code-breaking tool in the world, and today's article will extract a few common and commonly used parameters, combined with password-breaking commands, to analyze how to use hashcat to decipher passwords.
-m /--hash-type
We know that hashcat can decipher a large number of password types, it can decipher about 210 types of ciphers, the vast majority of which are hashes. If you want to decipher a password with hashcat, you first need to understand the form of the password, and then index the number of the password in the hashcat according to the password form.
Let's take the password: digapis and salt asdf as examples to show the form of some hash values.
| numbering | name | type | example |
|---|---|---|---|
| 0 | MD5 | Hash, length 32 | 8713d75511bea7e0df78c6063dc778b0 |
| 1400 | SHA-256 | hash | aa106625c7de812d6118992a191ea4627e2457fa80bf6ec06f9c60cbf8e5260f |
| 1700 | SHA-512 | hash | 23afac4524f62ea4d941ca4933249b2b78d19069773266abc36d6fd17a6fbe2f4ccc834acc868358ba32ddca553611218a2865f975339fe45d38cc1999f84b5e |
| 10 | Md5($pass.$salt) | MD5 is performed once after the password is salted, with the password first | 48985c61e2581c3f9ee5f1cfb775afbc:asdf |
| 20 | MD5($salt.$pass) | Salt first | 4fa1dd606353e055fed67d9812bddf35:asdf |
| 2600 | md5(md5($pass)) | The password is MD5 2 times | 98177c3f36af4a3f77f5b87594e6cf6a |
| 3710 | md5($salt.md5($pass)) | The password is MD5 transformed, preceded by salt, and MD5 is performed again | 88a535877ec21b8786775a7074e4de4c:asdf |
| 4400 | md5(sha1($pass)) | The password is changed once sha1 and then MD5 | ec7bf3099984001a2b0f37ba5d1d68fa |
| 4500 | sha1(sha1($pass)) | outline | 005a41cfe16c9a5556c7a5cdd5f1958991f2e031 |
| 1460 | HMAC-SHA256(key=$salt) | outline | d684ab7c38ddc262f215328334c4d0273cef10d6c5e61988f5cc87fcab8a7a60:asdf |
| 11500 | CRC32 | outline | 4C244A19:00000000 |
-a/--attack-mode
The -a command can specify the attack mode. To use hashcat to decipher the password, it is not enough to know the password number, but also to select the attack mode of using hashcat to decipher the password.
Hashcat 4.0.1 has 5 attack patterns, each with its own characteristics.
| numbering | Attack patterns | meaning |
|---|---|---|
| 0 | straight | Direct attack mode |
| 1 | Combinstion | Combo attack mode |
| 3 | Brute-force | Explosive crack mode |
| 6 | Hybrid Wordlist+Mask | Dictionary + mask combination |
| 7 | Hybird Mask+Wordlist | Mask + dictionary combination |
In these 5 attack modes, we can use dictionaries to decipher, use brute force to traverse all possible passwords, or combine dictionaries and masks for code breaking. In different attack modes, the parameters used in the hashcat command are different, let's take the straight attack mode as an example to learn how hashcat uses dictionary files to decipher passwords. Colleagues will also intersperse the use of other parameters.
Direct Attack Mode (-a 0)
The direct attack mode is to directly use the dictionary to perform password blasting, which can use a single dictionary file or multiple dictionary files for decryption. You can also combine dictionaries with rule files to make password blasting more efficient.
Single Dictionary Attack:
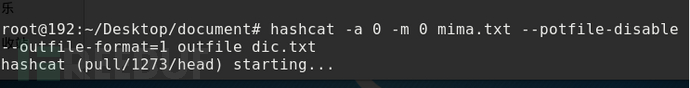
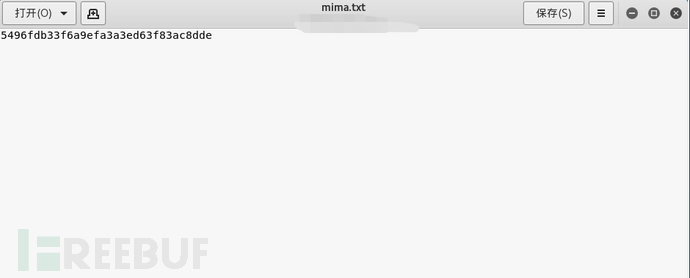
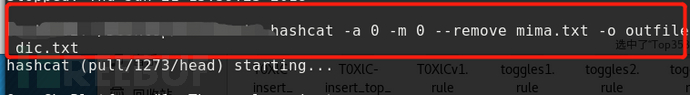
hashcat -a 0 –m 0 mima.txt –o outfile dic.txt
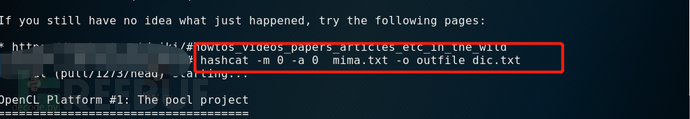
-a specifies the attack mode as direct attack, -m specifies the hash type as MD5, and -o writes the deciphered password to the outfile.
Double dictionary attack
A double dictionary attack is also a case of direct attack mode, in which two dictionary files are loaded when the password is blasted using the dictionary file. This expands the space of the dictionary file.
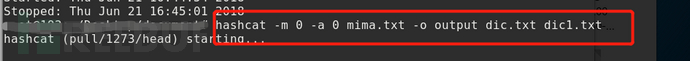
Multi-dictionary attacks
The following command uses three dictionaries to perform a dictionary attack, and loads three dictionaries in turn to blast. The dic.txt in the command is the dictionary file used in the blast.
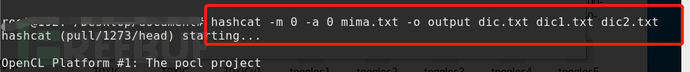
Dictionary directory attacks
The dictionary directory attack will use multiple dictionary files in the dictionary directory for direct attack, and the dictionary directory will load multiple dictionary files in the dictionary directory in sequence during the direct attack, and the dic in the following command is the folder where the multiple dictionary files are located.
Dictionary + rule attack
The -r/--rule-file command applies multiple rules in the rules file to each word in the dictionary. The rule file can be generated by yourself or by using the rule file that comes with hashcat. The rules file that comes with hashcat is usually located in the rules folder. The rules file in the rules folder is as follows:

In a dictionary + rule attack, a single dictionary, multiple dictionaries, or dictionary directories can be combined with rule files to perform password blasting. In fact, it is in the form of a direct attack and a combination of rules and documents.
Rules are similar to programming languages that generate candidate passwords, which can modify, cut, expand words, or skip actions based on conditional operators. In this way, attacks can be carried out more flexibly and efficiently.
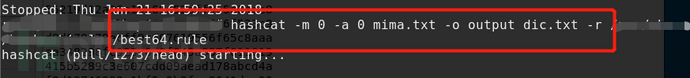 Rule attacks can be used in combination with dual dictionaries, multiple dictionaries, or even dictionary directories. The usage method is similar to that of a single dictionary + rule attack.
Rule attacks can be used in combination with dual dictionaries, multiple dictionaries, or even dictionary directories. The usage method is similar to that of a single dictionary + rule attack.
Output commands
-o/--outfile
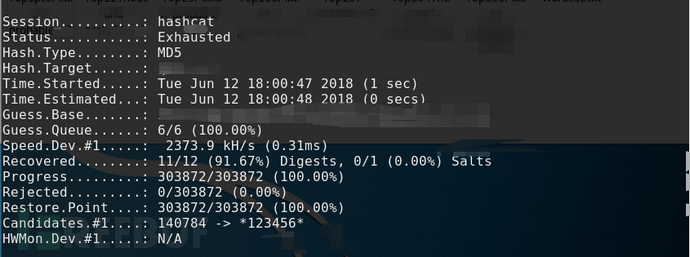
The -o parameter is followed by the outgoing file, and the deciphered password is entered into the specified file through the -o command, and the default storage form is hash:plain. There is an example of how this command is used, so let's take a look at the above picture for yourself.
--outfile-format
This command can specify the output format of the outfile file. There are 15 output modes in the Outfile file.
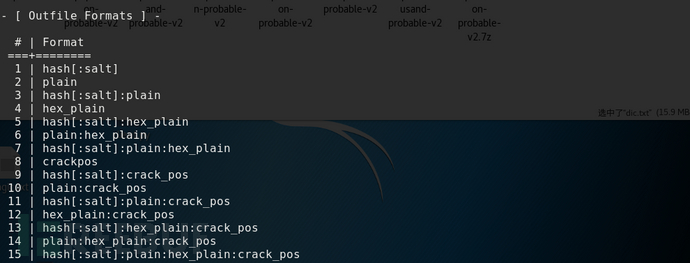
Outfile-format=1 only outputs the deciphered ciphertext hash;
Outfile-format=2, which outputs only the plaintext of the deciphered password.
--remove
In addition to using the -o parameter to output, we can also use the parameter remove to filter out the deciphered passwords in the ciphertext file, leaving only the undecipherable passwords. This reduces duplication of effort when code breaking is carried out later.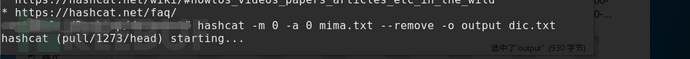
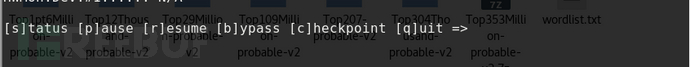
--status
When the number of password decipherment is large or the dictionary file is very large, the following options will appear, and the keyboard input S will print the next status on the screen, through which you can check the progress of the current password decipherment.
It will be troublesome to enter S every time you want to check the current password breaking progress, so you can use the status parameter to let the screen automatically update the status screen. Reducing the number of operations you need to do can also reduce false touches.
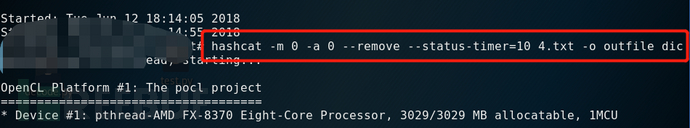
--status-timer
In addition to using the status parameter to automatically update the screen status, you can also use the --status-timer parameter to set the interval at which the status screen is updated.
summary
That's pretty much how to use the direct attack mode in Hashcat. If you are interested in hashcat, you can also visit the hashcat website, which has a detailed description of hashcat's command parameters and each attack mode.